Encryption in-transit
MongoDB Enterprise Advanced supports encryption in-transit using Transport Layer Security (TLS).
In Atlas, all network traffic to MongoDB clusters is protected by TLS by default. TLS cannot be disabled and the default version is TLS v1.2. Data that is transmitted to MongoDB clusters, as well as data transmitted between nodes of your MongoDB clusters, is encrypted in-transit using TLS.
Learn more about Encryption In-Transit →
Encryption at-rest
Encryption at-rest is a database-level protection layer to guarantee that the written files and data are encrypted while stored. MongoDB Enterprise Advanced (EA) has implemented the at-rest encryption in WiredTiger, the database storage engine, using AES-256. You can configure at-rest encryption in MongoDB EA with a KMIP-enabled key provider.
In Atlas, customer data is encrypted at-rest by default using AES-256 to secure all volume (disk) data. The process is automated by the transparent disk encryption of your selected cloud provider, and the cloud provider fully manages the encryption keys. You may also choose to enable database-level encryption, which allows you to bring your own encryption keys in AWS Key Management Service (KMS), Google Cloud KMS, or Azure Key Vault.
Encryption At-Rest → MongoDB Enterprise and MongoDB Atlas
In-Use Encryption
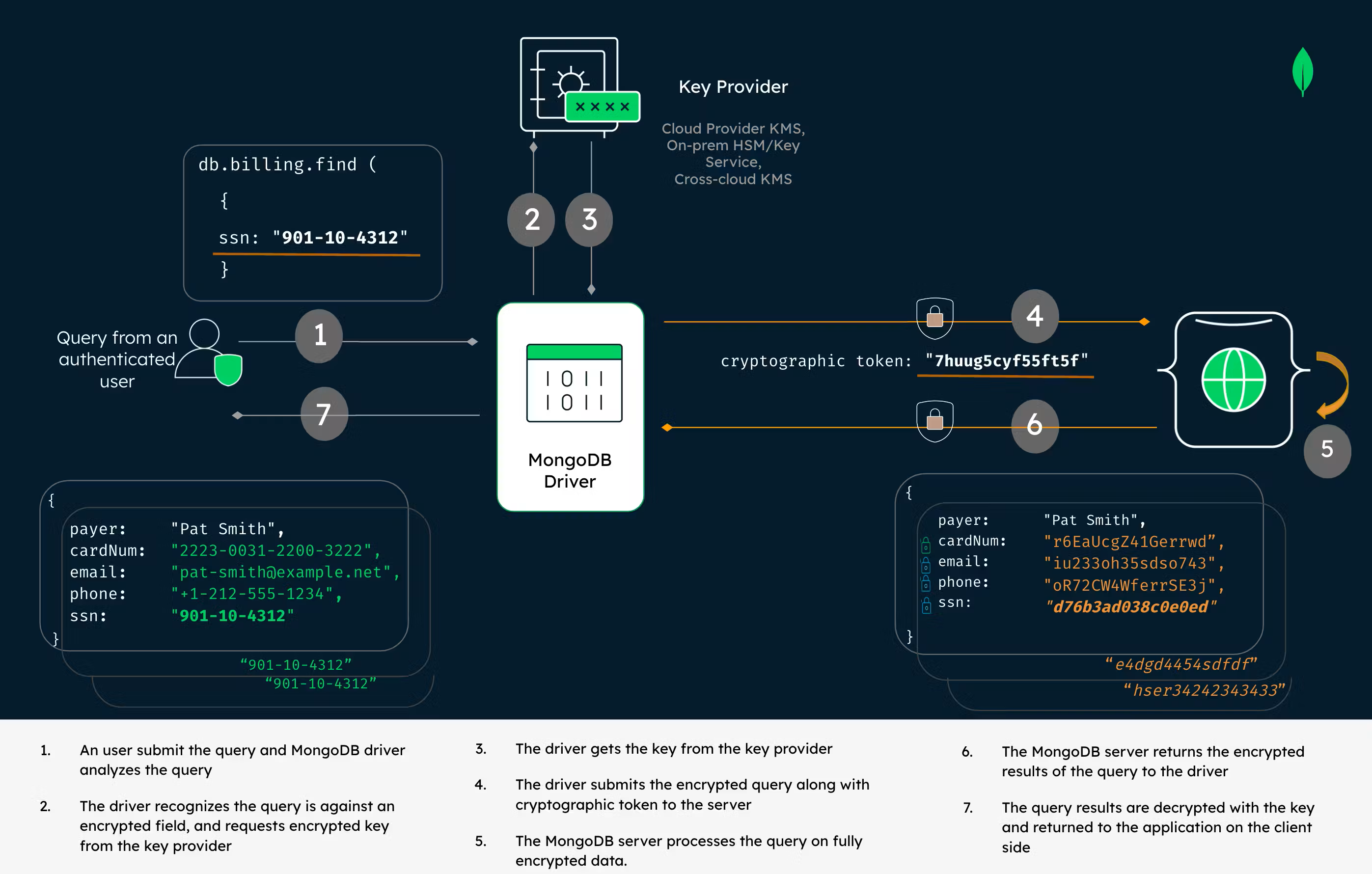
Data is encrypted client-side with customer-controlled encryption keys, before being sent, stored, or retrieved from the database. The benefits of this approach are:
- Data encrypted throughout its lifecycle
The strongest technical control to ensure that data always remains encrypted in-use, in backups, at-rest, and in-transit. - Faster application development cycle
MongoDB takes the complexity out of developing applications for sensitive workloads. Developers don’t have to be security or cryptography experts to build encryption into their applications. - Address critical data privacy use cases
Helps customers meet strict data privacy requirements such as HIPAA, GDPR, PCI, CCPA and more.
MongoDB has two features for encryption in-use to meet your data protection needs.